 I have decided to write on GSM security structure so that you people about the telecommunication world security, well before going to the main topic it is good to introduce the GSM.
I have decided to write on GSM security structure so that you people about the telecommunication world security, well before going to the main topic it is good to introduce the GSM. GSM or Global System For Mobile Communication is a digital cellular communication system that works on TDM(time-division multiplexing) and FDM(frequency division multiplexing) multiplexing technique, i will not discuss all the technique deeply because it is a another topic to be discussed, but it is necessary to review the design or structure of the system to whom we analyze.
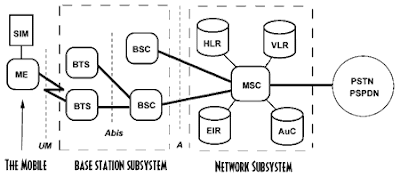
The first generation 1G mobile network has a different vulnerability including eavesdropping and handset cloning than in GSM including protection against these vulnerability. Below is a diagram which shows the basic architecture of Global System For Mobile Communication (GSM).
Here ME is your mobile set and BTS (Base Transceiver station) is the local tower that connect your handset to the network and send your request to the BSC(Base Station Controller) than there is MSC (Mobile switching center) that is responsible for the switching and routing in MSC there are AuC (Authentication center) HLR (Home location register) VLR (Visitor Location Register) and EIR (Equipment identity register).
HLR and VLR is a database that stores user(handset) data, VLR is a variable database and stores data for a short period of time while HLR is a permanent database and contain all the records of user.
GSM Security Basic
The SIM (Subscriber Identity Module) is a small and smart card contain both programming and information. SIM contain a temporary cipher key for encryption, temporary subscriber identity(TIMSI) and International Mobile Subscriber Identity (IMSI). It also contain a PIN (Personal Identification Number) and a PUK (PIN unblocking key).
SIM stores a 128-bit authentication key provided by the service provider, IMSI is a unique 15-digit number that has a three part.
- Mobile Country Code (MCC)
- Mobile Network Code(MNC)
- Mobile Subscriber Identity (MSIN)
The algorithm that has been implemented on SIM is A3 and A8 click here to learn A3 Algorithm and A8 Algorithm.
How The Network Identify SIM
Ki is the 128-bit Individual Subscriber Authentication Key utilized as a secret key shared between the Mobile Station and the Home Location Register of the subscriber’s home network.
RAND is 128-bit random challenge generated by the Home Location Register.
SRES is the 32-bit Signed Response generated by the Mobile Station and the Mobile Services Switching Center.
Kc is the 64-bit ciphering key used as a Session Key for encryption of the over-the-air channel. Kc is generated by the Mobile Station from the random challenge presented by the GSM network and the Ki from the SIM utilizing the A8 algorithm.
Note: If you enjoyed this post, you might want to subscribe our RSS feed and Email Subscription or become our Facebook fan! You will get all the latest updates at both the places.


No comments:
Post a Comment